The NSA and CISA are begging you: Stop making these cybersecurity configuration mistakes
The National Security Agency (NSA) and Cybersecurity and Infrastructure Security Agency (CISA) released a joint cybersecurity advisory (CSA)—also available as a separate PDF download—confirming the most common cybersecurity misconfigurations. The joint report includes Blue Team—which typically performs strategic vulnerability appraisals—and Red Team—which typically performs adversary emulation by testing security controls against hackers’ tactics, techniques and procedures (known as TTP)—assessments and mitigation recommendations.
Organizations continue perpetuating these dangerous cybersecurity mistakes
According to the agencies, these are the 10 most common cybersecurity misconfiguration mistakes organizations, including small and medium businesses (SMBs), make:
- Default configurations of software and applications
- Improper separation of user/administrator privilege
- Insufficient internal network monitoring
- Lack of network segmentation
- Poor patch management
- Bypass of system access controls
- Weak or misconfigured multifactor authentication (MFA) methods
- Insufficient access control lists (ACLs) on network shares and services
- Poor credential hygiene
- Unrestricted code execution
Subsequently, malicious hackers seize on these errors and commonly exploit the resulting vulnerabilities to penetrate networks, illegally access systems, steal information, corrupt networks and data and extract ransom payments from victims. The resulting damages, business interruptions and expenses often prove devastating, affecting everyone from small operators to government offices and even large multinational corporations across all industries.

CISA and the NSA have released a joint cybersecurity advisory, available as a downloadable PDF, that details the top 10 cybersecurity misconfigurations organizations commonly make.
It’s particularly poignant the agencies released the joint cybersecurity advisory (known officially as Alert AA23-278A) in October. A White House proclamation, seeking to prioritize information technology (IT) security, named October Cybersecurity Awareness Month.
Cybersecurity Mitigations Organizations Should Adopt
CISA, the NSA and other respected authorities (including the National Institute of Standards and Technology, often referred to as the NIST) and best practices prescribe mitigating common cybersecurity misconfiguration mistakes by adopting the following recommendations, as specifically listed within the agencies’ CSA.
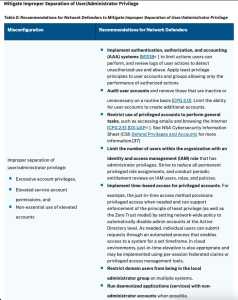
The joint CISA and NSA cybersecurity advisory lists specific and detailed mitigation recommendations for each of the top 10-most common cybersecurity misconfigurations.
Note, the steps CISA and the NSA recommend for mitigating common cybersecurity misconfigurations quickly become technical. Even if you don’t fully understand all the accompanying jargon or specific technologies referenced within the agencies’ mitigation recommendations, familiarizing yourself with the number and nature of these best practices can better prepare you and your organization for corresponding conversations with internal IT staff and outside technology service providers.
Mitigate Default Configurations of Software and Applications
- Modify the default configuration of applications and appliances before deployment
- Change or disable vendor-supplied default usernames and passwords of services, software, and equipment
- Ensure the secure configuration of Active Directory Certificate Services (ADCS) implementations
- Review all permissions on the ADCS templates on applicable servers and restrict enrollment rights to only those users or groups requiring them
- Determine if Link-Local Multicast Name Resolution (LLMNR) and Network Basic Input/Output System (NetBIOS) are required for essential business operations and disable them when possible
- Require Server Message Block (SMB) signing for both SMB client and server on all systems
Mitigate Improper Separation of User/Administrator Privilege
- Implement authentication, authorization and account (AAA) systems to limit actions user can perform and review user action logs to detect unauthorized use and abuse
- Audit user accounts and remove inactive or unnecessary accounts regularly
- Restrict use of privileged accounts to perform general tasks
- Limit the number of users within the organization with an identity and access management (IAM) role possessing administrator privileges
- Implement time-based access for privileged accounts
- Restrict domain users from being in the local administrator group
- Run daemonized applications (services) with non-administrator accounts whenever possible
- Only configure service accounts with the permissions necessary for the services they control to operate
- Disable unused services and implement access control lists (ACLs) to protect services
Mitigate Insufficient Internal Network Monitoring
- Establish a baseline of applications and services and routinely audit their access and use, especially for administrative activity
- Look for suspicious accounts, investigate them and remove accounts and credentials of former staff
- Establish a baseline that represents an organization’s normal traffic activity, network performance, host application activity, user behavior and investigate any deviations from that baseline
- Use auditing tools capable of detecting privilege and service abuse opportunities on systems and correct those vulnerabilities
- Implement a security information and event management (SIEM) system to provide log aggregation, correlation, querying, visualization and alerting from network endpoints, logging systems, endpoint and detection response (EDR) systems and intrusion detection systems (IDS)
Mitigate Lack of Network Segmentation
- Implement next-generation firewalls to perform deep packet filtering, stateful inspection, and application-level packet inspection
- Engineer network segments to isolate critical systems, functions, and resources
- Implement separate Virtual Private Cloud (VPC) instances to isolate essential cloud systems
Mitigate Poor Patch Management
- Ensure organizations implement and maintain an efficient patch management process that enforces the use of up-to-date, stable versions of OSes, browsers and software
- Prioritize patching and update software regularly by employing patch management for externally exposed applications, internal enterprise endpoints and servers
- Automate the update process as much as possible and use vendor-provided updates
- Consider using automated patch management tools and software update tools
- Segment networks to limit exposure of the vulnerable system or host where patching is not possible
- Evaluate the use of unsupported hardware and software and discontinue use as soon as possible
- Patch the Basic Input/Output System (BIOS) and other firmware to prevent exploitation of known vulnerabilities
Mitigate Bypass of System Access Controls
- Limit credential overlap across systems to prevent credential compromise and reduce a malicious actor’s ability to move laterally between systems
- Implement an effective and routine patch management process
- Enable pass the hash (PtH) mitigations to apply User Account Control (UAC) restrictions to local accounts upon network logon
- Deny domain users the ability to be in the local administrator group on multiple systems
- Limit workstation-to-workstation communications
- Use privileged accounts only on systems requiring those privileges
Mitigate Weak or Misconfigured MFA Methods
- Disable the use of New Technology LAN Manager (NTLM) and other legacy authentication protocols that are susceptible to PtH due to their use of password hashes
- Use built-in functionality via Windows Hello for Business or Group Policy Objects (GPOs) to regularly re-randomize password hashes associated with smartcard-required accounts
- Implement cloud-primary authentication solution using modern open standards
- Enforce phishing-resistant MFA universally for access to sensitive data and on as many other resources and services as possible
Mitigate Insufficient ACLs on Network Shares and Services
- Implement secure configurations for all storage devices and network shares that grant access to authorized users only
- Apply the principal of least privilege to important information resources to reduce risk of unauthorized data access and manipulation
- Apply restrictive permissions to files and directories, and prevent adversaries from modifying ACLs
- Set restrictive permissions on files and folders containing sensitive private keys to prevent unintended access
- Enable the Windows Group Policy security setting, “Do Not Allow Anonymous Enumeration of Security Account Manager (SAM) Accounts and Shares,” to limit users who can enumerate network shares
Mitigate Poor Credential Hygiene
- Follow NIST guidelines when creating password policies to enforce use of “strong” passwords that cannot be cracked
- Consider using password managers to generate and store passwords
- Do not reuse local administrator account passwords across systems
- Ensure passwords are “strong” and unique
- Use “strong” passphrases for private keys to make cracking resource intensive
- Do not store credentials within the registry in Windows systems
- Establish an organizational policy that prohibits password storage in files
- Ensure adequate password length (ideally 25+ characters) and complexity requirements for Windows service accounts and implement passwords with periodic expiration on these accounts
- Implement a review process for files and systems to look for cleartext account credentials
- Store hashed passwords using Committee on National Security Systems Policy (CNSSP)-15 and Commercial National Security Algorithm Suite (CNSA) approved algorithms
- Consider using group Managed Service Accounts (gMSAs) or third-party software to implement secure password-storage applications
Mitigate Unrestricted Code Execution
- Enable system settings that prevent the ability to run applications downloaded from untrusted sources
- Use application control tools that restrict program execution by default, also known as allowlisting
- Ensure that application control tools examine digital signatures and other key attributes, rather than just relying on filenames, especially since malware often attempts to masquerade as common Operating System (OS) utilities
- Explicitly allow certain .exe files to run, while blocking all others by default
- Block or prevent the execution of known vulnerable drivers that adversaries may exploit to execute code in kernel mode
- Validate driver block rules in audit mode to ensure stability prior to production deployment
- Constrain scripting languages to prevent malicious activities, audit script logs, and restrict scripting languages that are not used in the environment
- Use read-only containers and minimal images, when possible, to prevent the running of commands
- Regularly analyze border and host-level protections, including spam-filtering capabilities
Is your organization vulnerable to these common cybersecurity misconfiguration errors?
The nature of this latest joint cybersecurity advisory issued by CISA and the NSA is a little different from previous bulletins. This latest release is, in fact, almost a plea from seasoned cybersecurity experts for businesses and organizations to correct these errors. The mistakes, commonly exploited by cybercriminals, enable the continual perpetuation of damaging cybercrimes.
If your organization needs help better understanding its cybersecurity posture, making sense of the mitigation recommendations prescribed within the joint cybersecurity advisory or adopting best practices to better safeguard and protect its users, systems and data, call Louisville Geek at 502-897-7577 or email [email protected].



